Forge Platform
Forge is not a collection of security tools. It is a continuous trust system. Every feature in Forge:
Makes trust enforceable and easy to manage
Predicts trust failure before damage occurs
Acts autonomously when trust breaks
Aligns with leading control frameworks
No tickets. No runbooks. No waiting for humans to react.
Forge is Built to Contain the Entire Breach Lifecycle
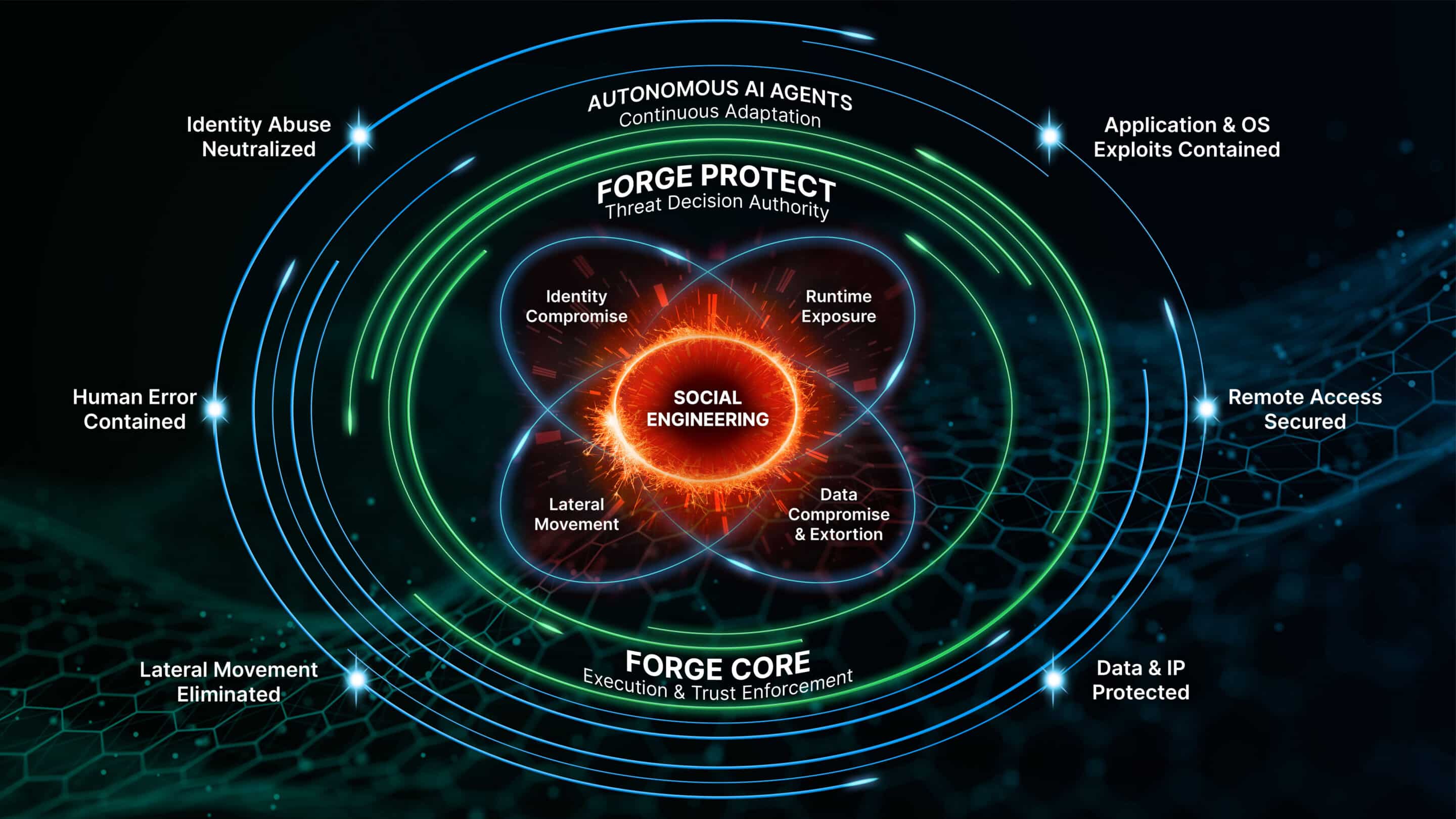
Modern attacks don’t begin with malware. They begin with exploited trust.
How It Works
Autonomous Prevention at the Edge
Forge delivers real-time prevention and segmentation by embedding trust directly into every connection, every execution, and every policy decision. Instead of reacting to alerts, Forge Prevent stops threats at the moment of execution across endpoints, cloud, and the network.
All decisions are powered by Forge’s internal intelligence engine, which continuously learns from system-wide trust signals to improve accuracy, speed, and resilience without centralizing sensitive data or introducing operational fragility.

Forge Core Makes Trust Real and Enforceable
Key outcomes:
• Identity-bound, cryptographic sessions instead of ports and IPs
• Trust enforced across users, applications, workloads, browsers, & AI
• Passwords, tokens, and session replay eliminated
• Micro-segmentation without VLANs or firewall sprawl
• Deterministic, human-readable policy enforcement
• Local enforcement on endpoints and servers
• Secure data-at-rest bound to hardware identity
If trust isn’t enforceable, it isn’t real.
Forge Core Features
| Capability | Included | Value |
|---|---|---|
| Digital Trust Layer (DTL) | Identity-bound, cryptographic sessions instead of ports/IPs | |
| Universal Trust Enforcement (UTE) | Enforce trust across users, apps, workloads, browsers | |
| TrustKey / Passkey Identity | Eliminates passwords, tokens, session replay | |
| VTZ Segmentation | Micro-segmentation without VLANs or firewalls | |
| Policy Engine | Human-readable, deterministic access control | |
| Forge Agents (Endpoint & Server) | Local, deterministic enforcement | |
| Secure Storage | Data-at-rest bound to hardware identity | |
| Basic Telemetry | Who accessed what, when, and why |
Forge Prevent Identifies Trust Failure Before Impact
Forge Prevent combines local execution-time enforcement with cloud-scale intelligence. Endpoints make immediate decisions based on real-time behavior, identity context, and trust state while continuously receiving policy and trust updates derived from system-wide learning.
This architecture enables execution-time prevention, resilience during connectivity disruption, and protection against zero-day and living-off-the-land techniques without creating centralized bottlenecks. Key outcomes:
• Behavioral baselines across identities and services
• Continuous trust scoring based on runtime behavior
• Detection of misuse of valid identities
• Prediction of high-risk trust conditions
• Discovery of unknown exploits and emergent attack paths
• Detection of configuration drift that silently expands trust
Most breaches begin with trusted identities behaving badly.
Forge Prevent Features
| Capability | Included | Value |
|---|---|---|
| Universal Trust Threat Prevention (UTTP) | Establishes behavioral baselines across identities, services, and trust zones | |
| Identity & Behavior Scoring | Continuous trust scoring based on real runtime behavior | |
| Trust Anomaly Detection | Surfaces misuse of valid identities and sessions | |
| Risk Prediction | Identifies sessions likely to result in trust failure before impact | |
| Cross-Tenant Signal Intelligence | Applies learned abuse patterns across environments | |
| Real-Time Inference | Sub-second research-grade analysis on live trust events | |
| Pre-Enforcement Risk Gating | Flags high-risk trust conditions prior to policy enforcement | |
| Dashboards & Insights | Explainable research findings, not opaque alerts | |
| Unknown Exploit Discovery | Discovers previously unknown exploit conditions and emergent trust violations | |
| Exploit Analysis | Identifies application vulnerabilities that materially degrade identity integrity | |
| Trust Drift Detection | Detects configuration states that unintentionally expand trust, weaken enforcement boundaries, or introduce privilege escalation paths |
Forge Trust Operations Executes Approved Trust Decisions at Machine Speed
Key outcomes:
• Autonomous policy adjustment
• Reflex-based enforcement
• Self-healing trust sessions
• Automated containment and isolation
• Playbook-free response
• Explicit human override boundaries
Security fails in the gap between detection and response. Forge removes the gap.
Forge Trust Operations
| Capability | Included | Value |
|---|---|---|
| Autonomous Policy Adjustment | Approved policies adapt automatically as trust conditions change | |
| Reflex-Based Enforcement | Machine-speed response without tickets or runbooks | |
| Self-Healing Trust Sessions | Compromised trust is revoked and re-established automatically | |
| Automated Containment & Isolation | Immediate isolation of identities or services violating trust | |
| Playbook-Free Response | Eliminates manual SOAR workflows | |
| Automation Engine | Operationalizes trust as a continuous control loop | |
| Human-Override Governance | Explicit approval boundaries for autonomous action | |
| Continuous Optimization Loops | System improves decisions over time without human tuning |
How It Works
Forge is a Continous Loop
Predict
Forge analyzes identity, behavior, and context to anticipate risk before access occurs.
Act
The system determines the correct trust response in real time based on current conditions.
Enforce
Forge agents enforce policy at the edge, allowing, limiting, or blocking traffic instantly.
Improve
Telemetry feeds back into Forge to continuously refine predictions and policies.
