Universal Trust Enforcement (UTE)
Enforce trust across identity, network paths, east-west traffic, and application access—continuously, not after the breach. UTE means:
Every request is verified
Observe & enforce in real time
Every connection is policy-checked
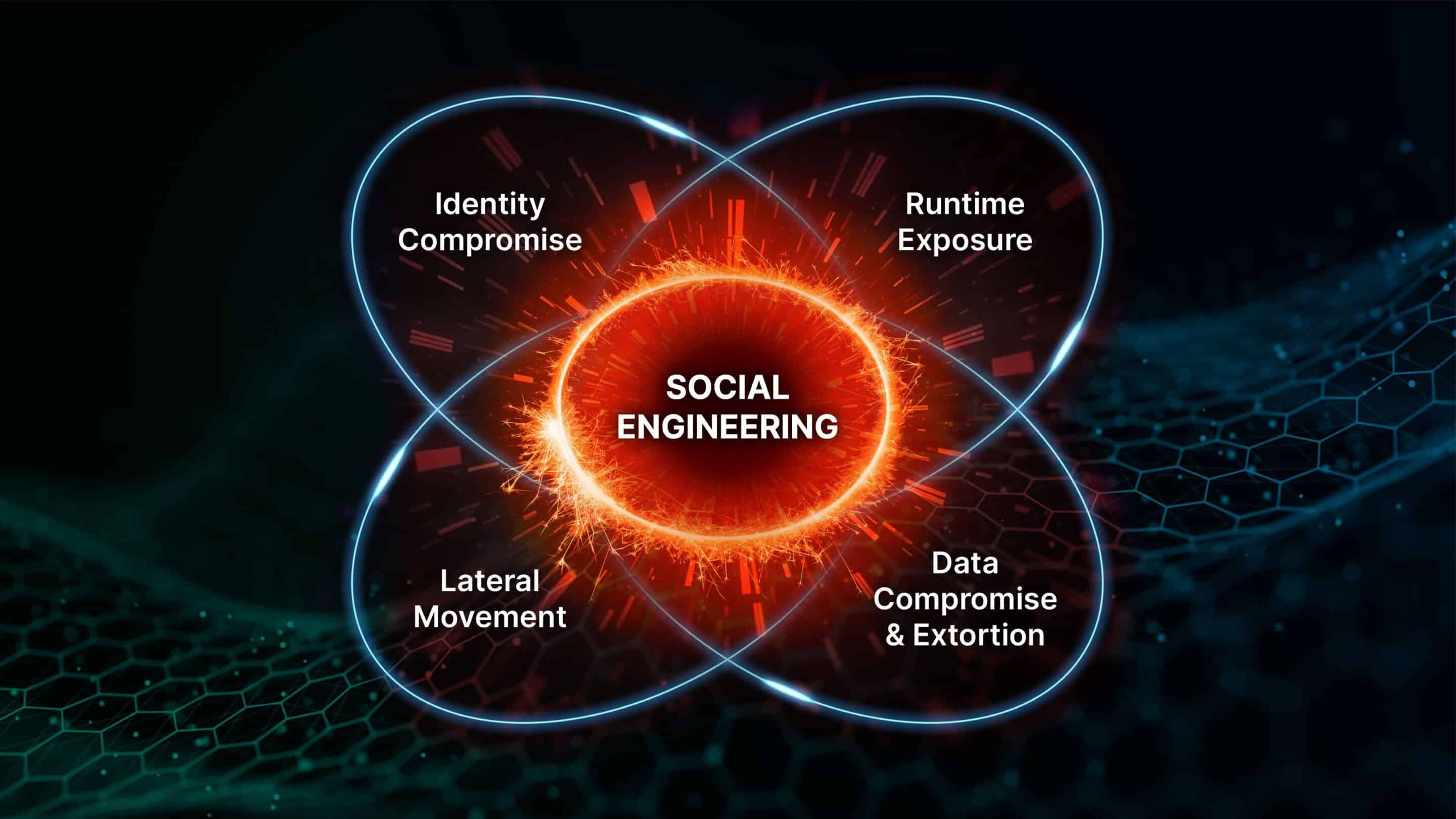
Social Engineering
90–95% of Successful Compromises Follow the Same Five Failure Paths
Modern breaches are not random. They repeat the same patterns, over and over
YouSource is architected to contain and neutralize each one by design
90% of Compromises Start with Social Engineering
YouSource designs for human error, not perfect behavior. All untrusted inputs, links, files, and actions are automatically isolated inside a Virtual Trust Zone, preventing a single mistake from becoming a systemic breach.
Identity Compromise
Forge binds every user, device, and service to a non-replayable identity. Stolen credentials, tokens, or sessions cannot be reused to impersonate trusted entities or expand access.
Runtime Exposure
Forge enforces trust at execution time. Processes and scripts are continuously validated against identity, behavior, and policy. Unsafe or abnormal execution paths are blocked or isolated before exploits can escalate, persist, or spread.
Lateral Movement
Trust does not propagate by proximity. Access is granted only through verified identity and policy, preventing compromised accounts or systems from expanding their reach across environments.
Data Compromise & Extortion
Forge enforces trust at execution time. Processes and scripts are continuously validated against identity, behavior, and policy. Unsafe or abnormal execution paths are blocked or isolated before exploits can escalate, persist, or spread.
Breaches do not cascade.
Compromise does not spread.
Attack paths collapse before damage occurs.
Dynamic Segmentation Powered by Trust Decisions
Forge replaces static network segmentation with dynamic, trust-driven isolation using Virtual Trust Zones (VTZ). Access decisions are based on identity, behavior, device posture, and trust score not IP addresses or network location.
As trust changes, access is automatically restricted or revoked. Lateral movement is contained by default, and segmentation adapts in real time as risk evolves.

What Forge Prevent Delivers
Forge is designed for environments where speed, precision, and resilience are non-negotiable. By unifying execution-time enforcement with cloud-scale intelligence, Forge Prevent delivers security that adapts as fast as modern threats evolve.
✓ Threats stopped at execution, not after detection
✓ Cloud-informed, locally enforced prevention decisions
✓ Automatic containment and adaptive segmentation
✓ Massive reduction in alert fatigue and operational noise
✓ Consistent enforcement across endpoint, cloud, and network
✓ Elimination of VPN and static perimeter dependencies
How It Works
Cloud-Scale Intelligence Without Centralized Fragility
While enforcement authority remains local, Forge continuously improves decision quality through cloud-scale learning. Anonymized trust observations flow upstream to refine policies, adjust trust scoring, and evolve prevention logic.
Improved intelligence is distributed back to endpoints as lightweight updates, strengthening protection everywhere without introducing latency, bottlenecks, or single points of failure.

The Pillars of Universal Trust Enforcement
A new trust model that enforces security before connection, not after compromise.

Enterprise-Scale Segmentation (East-West)
Forge is the world’s first UTTP engine, enforcing trust before any connection.
It replaces VPNs, SASE, NGFWs, and other reactive security tools.

Identity & Session Trust
Eliminate the value of stolen credentials by binding access to trusted sessions, not static identities or reused secrets.

Application Trust Enforcement
Application access is conditional and contextual—who is accessing it, from where, under what policy, and for what purpose.

TrustOps Telemetry & Fast Response
Trust telemetry is continuous and actionable. Detect trust drift and abuse quickly, then enforce automatically—within human-defined authority.
