Why Stolen Credentials Stop Working
Most security failures don’t start with malware. They start with valid credentials being abused.
Attackers don’t need to break in when systems are designed to trust tokens, cookies, and sessions by default.
The Core Flaw in Traditional Security
In most environments, credentials are accepted first and evaluated later. Once a token is considered valid, attackers can move laterally, escalate privileges, or exfiltrate data before detection tools ever react.
UTE Changes the Order
Universal Trust Enforcement reverses this model. Access is never granted until the source, context, and trust conditions are verified. Credentials alone are never sufficient.
Malicious Token Reuse Attemps
How Token Replay Fails with Universal Trust Enforcement
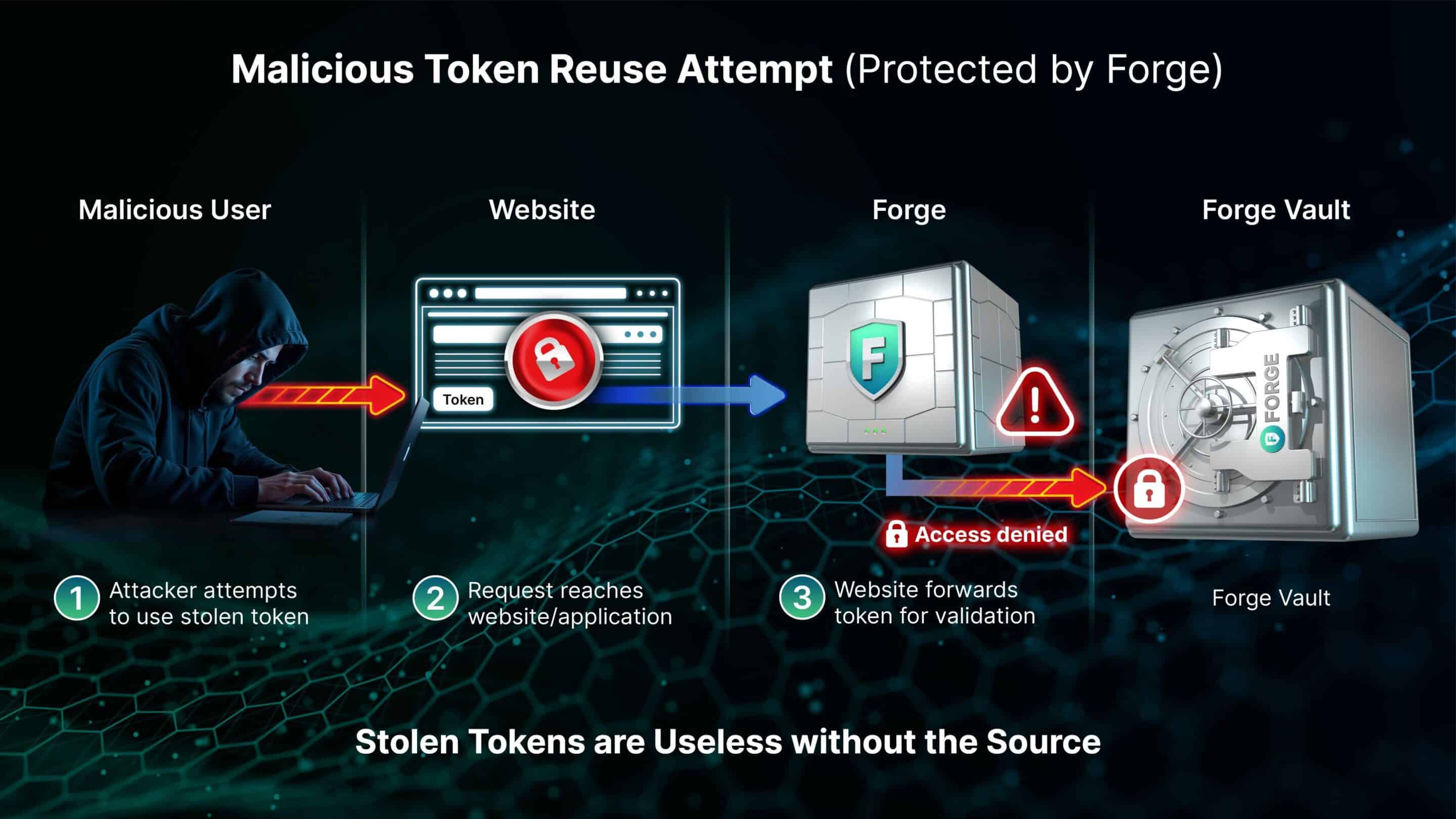
Step 1
An attacker attempts to reuse a stolen token.
Step 2
The request reaches the application but is not trusted by default.
Step 3
The token is forwarded for validation before any session is established.
Step 4
The source cannot be validated. Access is denied before damage can occur.
Forge prevents session hijacking, lateral movement, privilege escalation, and post-login abuse.
There is no trusted session to exploit and no cleanup phase required.
The Outcome
Stolen credentials lose their value. If the request does not originate from a trusted source, access is never granted.
If you’re not the source, there is no access. No exceptions.
